Top tips for people affected by the recent Yahoo security breach
On December 14 Yahoo announced a serious security breach in which sophisticated data attackers grabbed users’ answers to security questions, among other information such as names, email addresses, phone numbers, and birth dates. This breach is particularly worrisome because it culled sensitive information from 1 billion Yahoo customers, which makes this the largest data breach known to date. The breach happened in 2013, and many details about the breach remain murky. This is the second major data breach for Yahoo. One thing is certain: if you are a Yahoo customer impacted by this breach, some online clean up is in order. We’ve prioritized three key clean up items for you based on what we know right now.
1. First and foremost, change your passwords, security questions, and answers to your security questions on Yahoo and on your other key online accounts
If you are the rare person who uses a different password and security question and answer at each web site you sign on to, then you only need to change your Yahoo account information. But many people use the same or similar passwords and security answers at many online sites (even bank web sites!). It is especially common for people to answer security questions with the same answers across web sites. After all, the point of security questions is to help you remember the answers readily. Here are some common security questions:
-
What is your mother’s maiden name?
-
What is the name of the street you grew up on?
-
What is the name of your first pet?
All of us have our favorite answers to these questions, and that is what can decrease our security when we repeat those answers at multiple sites. Whatever answers you have given to Yahoo may well have been breached. The safest course of action is to change your answers to these questions at Yahoo as a first step. But if you have used the same answers pretty much everywhere, it is important that you make every effort to change your answers where you have used them. Prioritize financial, retail and health web sites first. For example, any online banking security answers should be top priority for changing, as well as answers on any credit card or other financial sites.
2. Be on the alert for clever phishing attacks
Be on the lookout for any kind of emails that ask you for your personal information. Period, end of discussion. Also be on the lookout for any other kinds of communications that ask for this information, like a text message, or an email that directs you to a web page that asks you for sensitive personal information. What might this look like? Phishing attacks have gotten pretty sophisticated, and they can take a lot of different formats. it can be hard to tell what is real and what is not. Here are some scenarios:
Issue: You get an unsolicited email saying your account has been breached, and that you need to click a link in the email itself to change your account password.
How to double check this: Don’t click the link in the email. Look for the name of the company in the message that is saying you have been breached, then do a search engine search for the company’s official website. Go to the website yourself, and sign in to your own account. Work on resetting your password directly from the official account. Don’t trust an unsolicited link. You can also call the company directly and ask them about suspicious emails, or see if they have an official Twitter feed that you can also check. Sometimes, links are shortened and put in a type of code that makes them hard to read. If this is the case, you can use a bit.ly decoder to untangle these and see the real links. (See Tips for motivated users below for more on how to use these decoders).
Issue: You are cruising around online, and all of a sudden, you get a pop-up notice on a webpage from a company saying that your computer or mobile phone has been attacked by malware, and that you need to call customer support immediately. There is a phone number for you to call.
How to double check this: Don’t call the provided phone number. Again, look up the company’s official webpage online through a search engine, and call their official phone number listed on their website. Tell the company what message you are seeing, and relay to them any error code the message is giving you. Some of these types of scams will simply be trying to scare you into purchasing a virus protection product. You can also check on the phone number via a phone number lookup app. For more on these types of apps, see the Tips for motivated users section below.
There are many possible scam and phishing scenarios after a data breach, but most of them involve getting you to click links, fill out forms, and provide further account or sensitive information. Sometimes scammers will ask for information via texting, sometimes they will ask that you call a phone number. After you have been subject to a data breach, you need to be especially cautious about any kind of information request like this. If you are asked to change your password or security question or security answer, take a moment. The email/website/text can wait while you make sure it is real. See more about this in the next section.
3. Be careful, scams have gotten a lot better
Some of the scams we are are seeing these days are quite convincing. You may not be able to recognize a fraudulent request for a password or other information right away. Here are some key red flags to watch for:
-
Is someone asking you to change your password? (And are they giving you a link to change it?)
-
Is someone asking you to change your security questions and answers? (And are they giving you a form to fill out or a link to follow to do so?)
-
Is someone asking for you to change your bank account sign on, or your account information at another company? (And are they providing a link in an email to do so?)
These are potential red flags, and if you are a Yahoo customer from 2013 to the present, we encourage taking extra caution with any such request. If you get unsolicited requests for your personal information, or requests to change your account password and security information, red flag these requests. Slow things down and be sure to find the official company web site before making any changes. If possible, sign in to the account in question and look for official communications from the company, for example, a company blog post, or other communications directly from the company to you. When in doubt, call the company directly from the phone number the company provides on its official page.
Tips for advanced users, or for motivated users
Here are additional tips for you. They involve a few extra steps, but are well worth exploring.
Authentication beyond passwords: Some websites and applications give you the opportunity to use additional layers of protection that go beyond passwords. For example some accounts allow you to use an extra authentication tool in addition to a password, or sometimes a site will let you use a mobile authentication tool that actually replaces a password. Yahoo offers a tool for its customers that replaces passwords. Yahoo calls it the Yahoo Account Key. Instead of using a password to access your account, you will get a code sent to your mobile phone to sign in to Yahoo. If you have not used a tool like this before, it may take some adjustment. But we encourage you to experiment with these kinds of tools, because they can greatly improve your account security.
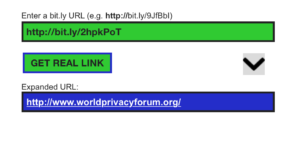
Decode shortened web addresses: If you have gotten an email with a link you are supposed to click, many times the link is shortened using bit.ly. We put www.worldprivacyforum.org into a bit.ly URL shortener, and our link looked like this: http://bit.ly/2hpkPoT. If you see a bit.ly link like this in an email, you can use a Bit.ly decoder to see the real URL. Here is a decoder that is simple to use. Copy the bit.ly URL you have received in an email or text (copy, don’t click!), then paste it into the bit.ly decoder of your choice. You will be able to see the real URL address.
Here, above, you can see a bit.ly decoder in action. We pasted our shortened World Privacy Forum URL in the top green box and then clicked the “get real link” box. In the blue box at the bottom, you can see the expanded URL.
Check out phone numbers with an app: To check phone numbers, there are a variety of apps that help with this. One is MrNumber; using this app you can look up numbers to see if they are fake. MrNumber has an interesting reporting feature; users can report spammy calls and phone numbers, it’s essentially crowd-sourced fraud and spam notices.
More information for Yahoo customers
Yahoo has published more information about its data breach, and they have also published security suggestions for their customers. Yahoo is suggesting that customers affected by the breach take the following steps: (This information is quoted from Yahoo’s blog post about the breach — the full notice is available here. )
- Change your passwords and security questions and answers for any other accounts on which you used the same or similar information used for your Yahoo account;
- Review all of your accounts for suspicious activity;
- Be cautious of any unsolicited communications that ask for your personal information or refer you to a web page asking for personal information;
- Avoid clicking on links or downloading attachments from suspicious emails; and
- Consider using Yahoo Account Key, a simple authentication tool that eliminates the need to use a password on Yahoo altogether.
Yahoo has a safety center, it is located at https://safety.yahoo.com. A good resource within the safety center is a security article that directs you to specific help for phishing or other account security issues. That article is here: https://safety.yahoo.com/Security/SECURITY_RESOURCES.html.
And finally, we want to give you one last word of encouragement to dig in and change your security answers. We have heard from some people that going through all web sites to make this change is just too overwhelming. We agree. Prioritize changing the security questions and answers first at Yahoo, then at your bank, credit card companies, and health care providers. If you have a lot of online retail purchases, that would be another good place to prioritize.