Consumer Tips: Search Engine Privacy
People often view search engines as blank boxes to which they can pose any question they want without any consequences. Unfortunately, this is not always the case. There is some art to searching online skillfully, and privately. Search engines large and small typically keep logs of users’ search terms. Some search engines match search terms to your computer address, your name, and other items, depending on how much information you have shared with the search engine. Using the right search engine in the right way takes skill, and this skill is relatively easy to learn and develop.
A first basic tip is to be especially aware that there are many kinds of search boxes online nowadays, and know that not all search boxes are tied to major search engines like Google or Yahoo. Some search boxes can be linked to fake search sites, which can in turn be laden with viruses. This is an ongoing problem for unwary web surfers.
Before you type your search terms into a search engine box, please be aware of the potential consequences. Unwary searches can come back to haunt you in a variety of ways, but basic search engine skills will go far to keep this from happening. Here are some simple steps you can start to take right away, on your very next visit to a search engine.
General Tips for Using Search Engines
We begin with general tips; for more detailed information read the expanded headings for new, intermediate, and advanced computer users. You can use as many or as few tips as you wish, but we recommend that everyone practice tips #1 and #2 in the list directly below. If you are using a wifi connection or a mobile device for searching, we highly recommend using tip #5, too.
- Use a legitimate search engine. Make sure you use a legitimate search engine. We are seeing an increase in “fake” search engines masquerading as the major brands and luring in inexperienced users. There’s more on this issue in the expanded information below.
- Watch what you search for. Don’t type in your name followed by your full SSN or government ID number.
- Mix it up. Use a variety of search engines. This can make a big difference over a long period of time. What would someone know about you if they could see all your searches from the last year? Or the last three years?
- Delete cookies from time to time. Cookies can be used to correlate a variety of information. If you do use cookies, delete them from time to time and start fresh. Once a month is a good starting point. An accessible geek discussion of cookies is here.
- Use encrypted search. Especially if you are searching on a mobile device or over a wifi connection, make sure you are searching on an encrypted connection. The connection will read https:// in the URL bar. If you don’t see https, don’t do any serious searching.
- To sign in or not? If you regularly sign in to a search engine’s personalized accounts or services, that will usually tie all your different devices and locations together. This may be something you want so that your devices are synced. If you like to sign in, we still recommend that you mix up your search engines from time to time by using a variety of major and minor search engines, or use a no-logs search engine like DuckDuckGo for sensitive searches.
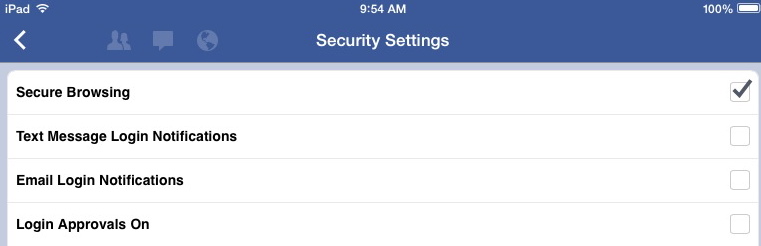
- Mobile search privacy. Use search engines that let you search using encrypted connections. This is crucial in mobile search privacy. Examples: Google is now encrypted by default, as is DuckDuckgo. This is a positive development. See https://encrypted.google.com. You can also use https://duckduckgo.com for no logs. If you are searching through a mobile app, for example searching for a friend through the Facebook app, the same applies: make sure your searches are encrypted when possible. This is now an option set on by default on Facebook, but you should still check. To see this option, in Facebook go to Account Settings —> Security –> and then put a tick in the Secure Browsing box if it is not already there (See screenshot 1). (You get bonus mobile privacy points if you have opted out of CPNI sharing from your mobile provider. Check the privacy policy of your mobile provider to find out how to opt out of that. CPNI is not directly related to search privacy, but is related to mobile privacy generally.
- If you are an advanced computer user, you can explore VPNs and proxies. See our discussion of this in the expanded headings below.
- Wifi users should use encrypted connections and encrypted search… no matter what kind of device you are using. If you use the Firefox or Chrome browser, you can use a plugin called HTTPS everywhere to facilitate encrypted connections. See https://www.eff.org/https-everywhere. Another plug in for Firefox is HTTP nowhere, which blocks unencrypted connections. See https://rx4g.com/http-nowhere/
- If you are extremely serious about search privacy, use the Kitchen Sink approach. That is, your best bet is to use as many of the above tips as you can. Use VPNs and proxies, use encrypted search, use HTTPS everywhere, delete and manage all of your cookies at an advanced level. (See our cookie management tips here for more on this). Routinely use a wide variety of computers, mobile devices, connections, and search engines. Very few people will employ these levels of tactics for long periods of time because it is very difficult to maintain. Choose what is sustainable for you.
(1) Facebook’s Secure Browsing setting for mobile. Go to Account Settings –> Security —> tick the Secure Browsing box if it is not already on. Your device will browse with secure connections when they are available.
For those new to online browsing: use a reputable search engine
A reputable search engine means that the search engine you are using is well-known, uses good security, and is not scammy. We added this tip after we kept hearing from consumers who had been tricked into using a virus-laden fake search engine. We hear from far too many people who have been tricked into typing queries into a fake search engine to treat it as just a fluke.
So — if you are new to online browsing, didn’t grow up with a computer, or feel in any way like a newbie to computers and privacy, we recommend that you stick with well-known search engine brands for your searching.
Some examples of major search engines, alphabetically:
- Bing
- Google (Encrypted by default)
- Yahoo
Additional examples of reputable search engines:
- DuckDuckGo (Encrypted by default, does not keep logs )
- Startpage (deletes IP address after 48 hours)
- Wolfram Alpha (Math-science-statistics focused search engine)
There are literally hundreds of search engines online. There are many more reputable search engines than we have listed — we can’t list them all here, and we haven’t listed some of the big international search engines that are country-specific.
We know that you may see ads at some of the major search engines, and this may be pesky to you. However, we have not received consumer complaints of serious viruses from just visiting or typing in a query at reputable search engines, and that is the point of this tip, to avoid “fake” or imposter search engines.
We have generally noticed that the “louder” a search engine is visually, the chances of it being invasive or threatening are higher. So if you see blinking and flashing search engines with a lot of windows popping up at you, it is best to leave these sites alone. If you are new online, it is better to be safe in this instance than adventurous. There is a very good article on this issue here.
For everyone: More on “Watch what you search for”
When you search online, avoid using terms that include your full legal name together with information that you don’t want someone else to have. For example, searching for your full name and your full Social Security number (or ID card number) within one query is not optimal. If you have conducted this search, then your name and your SSN (or other unique identifier) will appear together in the search string, and may be stored for a long time.
For example, if you search for ” Jane Doe 123-45-6789,” with the 123-45-6789 standing in for a real SSN, at Google, the search string will look like this: (we have highlighted our search term in red so you can see it more easily.) https://www.google.com/#q=%22+Jane+Doe+123-45-6789%22+
The same search at DuckDuckGo looks like this: https://duckduckgo.com/?q=%22+Jane+Doe+123-45-6789%22+k
The same search at Yahoo! Looks like this: http://search.yahoo.com/search;_ylt=AmM2LOBhiEEhpMLnv2Fw88SbvZx4?p=%22+Jane+Doe+123-45-6789%22+&toggle=1&cop=mss&ei=UTF-8&fr=yfp-t-900
Jane Doe’s name and SSN are in the search string in all examples, so this is a search that you won’t want to be conducting because it leaves behind too much information about you. This is especially true if you are using an unencrypted connection. (Your address will read http:// if the connection is unencrypted. If the connection is encrypted, it should read https://) In the example above, Google and DuckDuckGo searches are encrypted.
Many individuals conduct this kind of name-SSN search in order to make sure that their name and SSN does not appear somewhere on the Web. It is actually a good idea to look for this information, and people have discovered security breaches using this kind of search. But it is better to conduct this search with just your name and only the last 4 digits of your SSN or last digits of any other government-issued ID. This abbreviated search will retrieve the same information, and in the process you will keep your information safer.
So, before you search, think. Other people may someday see those search terms. In 2006, AOL released about 20 million search queries of over 500,000 of its users. [1] Those queries were put on the web. Reporters for the New York Times were able to identify a user from the search queries; others have also been able to identify users. [2]
Also, be aware that governments may be interested in your search terms and clicks. In 2013, the Guardian newspaper published a series of substantive articles about the United States’ National Security Agency’s wide-scale capture of Internet communications. Previous to this, in 2005, the U.S. Department of Justice subpoenaed Google, Yahoo, MSN, and AOL for tens of millions of users’ search queries. Google successfully fought the request, and was able to limit its disclosure, but it is unknown how much data other companies may have turned over in response to other legal government requests.
The federal government can force a search engine to turn over your searches, if that data is stored there. So can someone suing you. If you are involved in a divorce or child custody case, your search records can be used against you. There is a special term for this privacy issue, it is called “data retention.” In some countries, there are data retention periods for communications providers for cybersecurity purposes, A good overview on this is available at: http://wiki.openrightsgroup.org/wiki/Data_Retention.
Special note about passwords and user names:
Do not type passwords or user names into search engines. If there is a security breach that allows your data to be released to others, these passwords and user names can potentially be used to identify you, or even potentially cause some mischief. If you have already typed your favorite passwords or user names into a search engine, it is a good idea to change your passwords and user names. When AOL had a major breach of its search engine, we analyzed the results and found many people had typed their user names and passwords into the AOL search engine. This information was essentially made public by AOL in its breach.
For Everyone: Encrypted Search
Search engine encryption is very big news in the post-Snowden, post-NSA revelations world. There is a lot to say about this, and a full discussion exceeds the boundaries of this tipsheet.
Our basic tip is this: we strongly urge all mobile device users and those using wifi to use encrypted search only. We also urge all laptop and desktop computer users to use encrypted search. Google and DuckDuckGo encrypt their searches by default now, so there is no longer any excuse.
The reason for using a default-encryption search engine is so that your communications provider does not get the information as it passes through their network … including search terms.
For a flavor of some of the discussions of encrypted search, see these posts on the topic:
Search Engine Watch discussion of encrypted search
If you want, you can go a step further and use encryption on all of your web browsing. If you use the Firefox or Chrome browser, you can use a plugin called HTTPS everywhere to facilitate that https://www.eff.org/https-everywhere. Another plug in for Firefox is HTTP nowhere, which blocks unencrypted connections. https://rx4g.com/http-nowhere/.
For Intermediate and Advanced Users: Consider using an anonymizing tool or a proxy
This is an advanced user tip. If you have good computer skills, the simplest way to disassociate yourself from your search terms is to use an anonymizing tool. There are free services available that allow you to use the Web without revealing your computer address, and there are also pay services. If you have a particularly sensitive search term you want to type in, or if you simply want to ensure that your searches are not attached to your computer’s Internet address, you may want to consider using one of these services.
You may not realize it, but your computer discloses a lot of information as you traverse the Web. To see your computer or IP address and the kind of information your computer is disclosing, visit StayInvisible.com http://www.stayinvisible.com. You may be surprised at how much information your computer or device leaks. Your computer’s address is just a series of numbers, but those numbers can be tied to you through a series of steps. Do you remember the RIAA lawsuits over music filesharing? The RIAA first found users’ IP or computer address, then went to Internet Service Providers to find out what specific customer that address belonged to. To reduce this exposure, reduce the information leakage from your computer.
- Anonymizer.com has a pay service and a free service. https://www.anonymizer.com/
- TOR Onion Router and Privoxy http://tor.eff.org http://www.privoxy.org/ TOR is a free tool you [ 1] can install on your computer that, when used in combination with a tool called Privoxy, helps to mask your computer’s address, among other things. It does take some technical know-how to install and maintain TOR and Privoxy, but it is not impossible for novice computer users to use. TOR can potentially make your Web surfing slow at times. However, TOR and Privoxy are a good tool set and are well worth considering. These two tools should be used together. TOR will not be immune from government snooping, but that is a different issue, and broader than this tipsheet.
- Anonymouse.org is an ad-based service. It is free, but there are ads. http://anonymouse.org/ Anonymouse is available in English and in German.
If you would like to try one of the anonymous proxies, please be aware of one caution: do not use a proxy found on this list (or any other list) to send a password or to conduct online banking. While an anonymous proxy can shield your computer’s address from search engines, unless you are completely sure of the source of the proxy server, then don’t trust the proxy with passwords or sensitive financial data.
One search engine we have found that to date keeps minimal logs is DuckDuckGo.com as well as Startpage.com.
Conclusion
It is challenging to achieve 100 percent privacy 100 percent of the time when using search engines online. In some ways, a lack of privacy is built into the current system. Using various tools and techniques, you can diminish the privacy issues. It’s better to think in terms of reaching achievable, sustainable privacy goals.
Instead of trying to remain anonymous on a search engine 100 percent of the time, which is not really possible unless you are seriously technically capable, aim for staying semi-anonymous some of the time. You may not have time one morning to surf anonymously through TOR or Anonymizer. When that happens, aim to use a variety of search engines with cookies turned off so that at least you aren’t creating an unbroken trail or history at one search engine. Especially if you wouldn’t want someone else to see what you are searching for, use a privacy protective search engine. In short, find the balance that works for you, but at least work to add privacy in to your search routine in some way. We encourage everyone to use encrypted web search when available.
And finally, this tipsheet has not considered your personal computing hygiene. You should regularly reset and clear your Web browser history, and remove searches that are stored in your browser’s cache. You can find the tools do delete your cookies or clean your browser’s cache in the menu of your Web browser.
As you browse the Web and conduct searches, keep in mind that those search terms are not merely floating into nothingness. In reality, they can be stored somewhere, and may be stored for a long time. And again, one last time, when possible, use an HTTPS connection, or secure connection, when you are using the web. Working to prevent privacy problems in the here and now is preferable to trying to clean up privacy problems after the fact.
—–
Endnotes:
[1] Saul Hansell, “AOL Removes Search Data on Vast Group of Web Users,” New York Times, August 8, 2006.
[2] Michael Barbaro and Tom Zeller Jr., “A Face Is Exposed for AOL Searcher No. 4417749,” New York Times, August 9, 2006.
Publication history:
Author: Pam Dixon
Updated October 2013, February 2012, March 2011, July 14 2008, July 8 2008, January 4, 2008, August 17, 2006; January 31, 2006. Posted January 20, 2006.